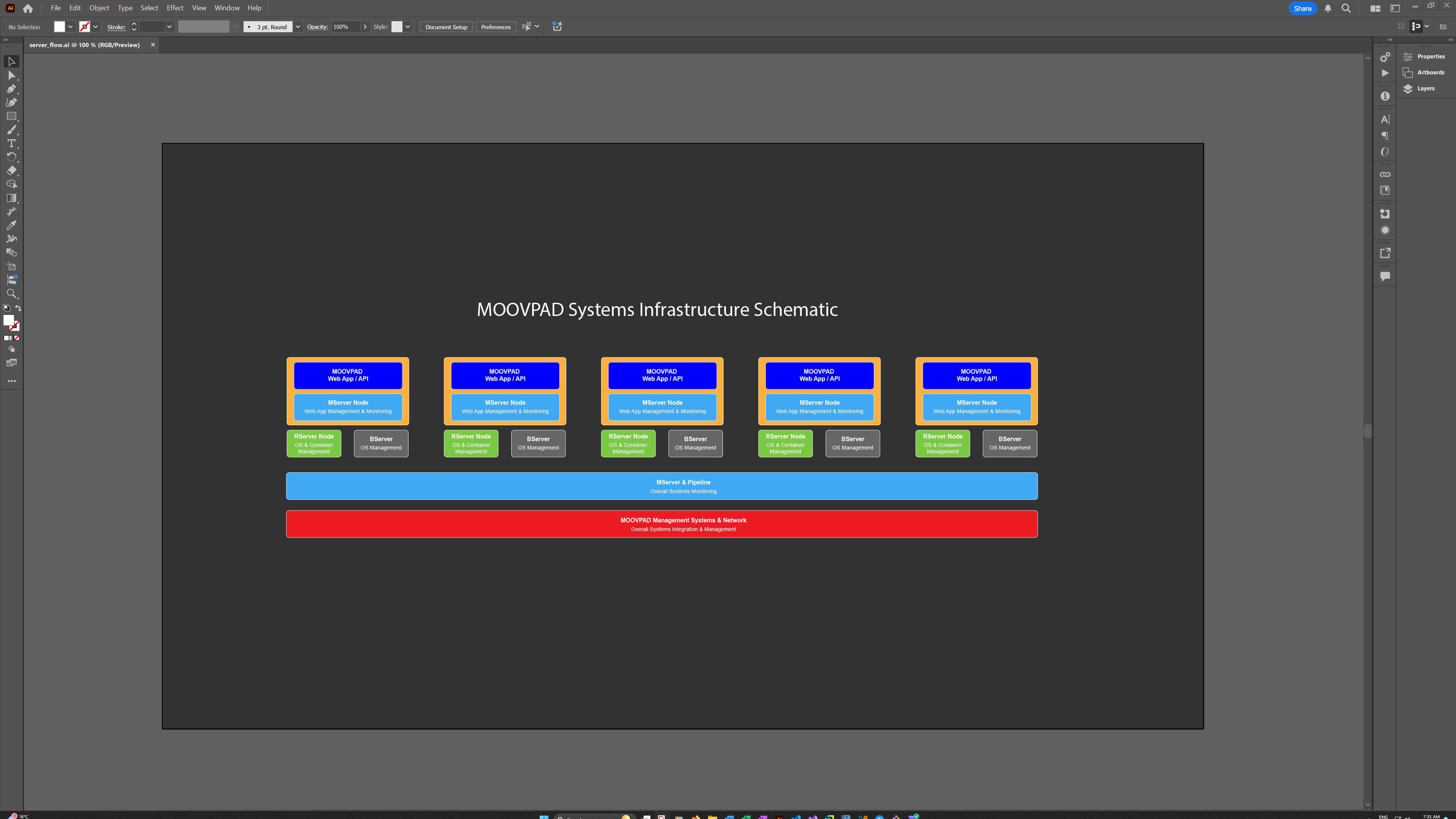
Clearer Picture At Each Level
Although there are some elements that I can't disclose, we have seen many of the pieces that will make up the MOOVPAD server and VM software systems. Over the past week or so, I've had a chance to do some initial testing with all of these components and shared the results with you here where possible. As a summary, the next section is a list of things we've looked at together in addition to external 3rd party WAFs like CloudFlare:
- Ubuntu Pro - Patch management & Hardening
- OpenScap & OpenVAS for standards & audits
- Iptables + Custom RServer VM firewall
- Suricata - IDS with added custom IPS rules
- SSH Guard + Custom RServer - SSH protection
- Site-Site VPN for secure communication
- Regular RServer for maintenance (things like running checks with Rkhunter, AppArmor, ClamAV, Auditd, Nmap and more)
- Multi-level encryption (hardware, DB's, RServer + MServer features)
- Hosted WAF: NAXSI vs custom MServer only
- ZenArmor - potential add-on if needed
All of these features and more will be integrated into the MOOVPAD management system that will be operated by the relevant teams, with the assistance of automated (and perhaps some AI) elements to support their work.
Plenty more work left to do, but good progress, yeah? 🙂
Stay awesome,
EMH
HOW MOOVPAD IS BEING BUILT
For the overview of how MOOVPAD apps are being developed, the reasoning behind particular decisions during development, policies, and more in relation to all the technical things, please see the link to the left.
This will be an ongoing work in progress, and will always be linked to the bottom of each upcoming Blog post.
