Initial Processes In Place
In my last post, I mentioned that I'd be looking into two sets of frameworks and tools. The first of these was OpenScap which is an open-source audit based on the Security Content Automation Protocol (SCAP), a standard maintained by the National Institute of Standards & Technology (NIST). Since that post, I've been able to ensure that all MOOVPAD servers will be compliant with this standard from day one.
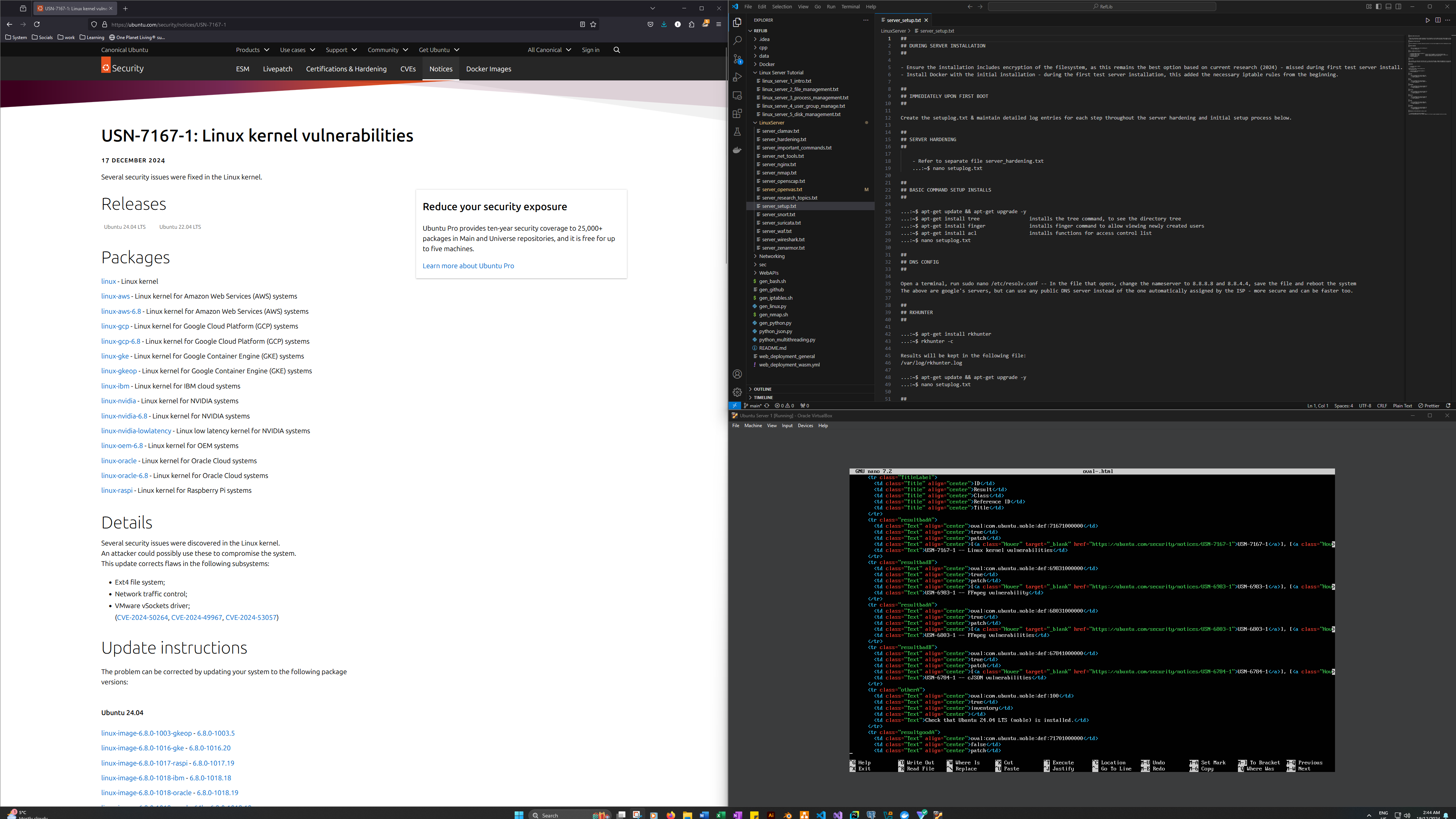
I don't yet have the physical test server hooked up for screen capture, but the screenshot above shows the results of testing on the VM I'm using for the first rounds of testing. As we can see, the scan revealed 4 vulnerabilities, one of which was not found on the physical server. The reason for that is my insistence on running the "apt-get update && apt-get upgrade' command after any major work and when I first boot the server. That helped with the linux kernel vulnerability. And the remaining ones require live-patching through Ubuntu Pro, which is the support program I mentioned a few days ago.
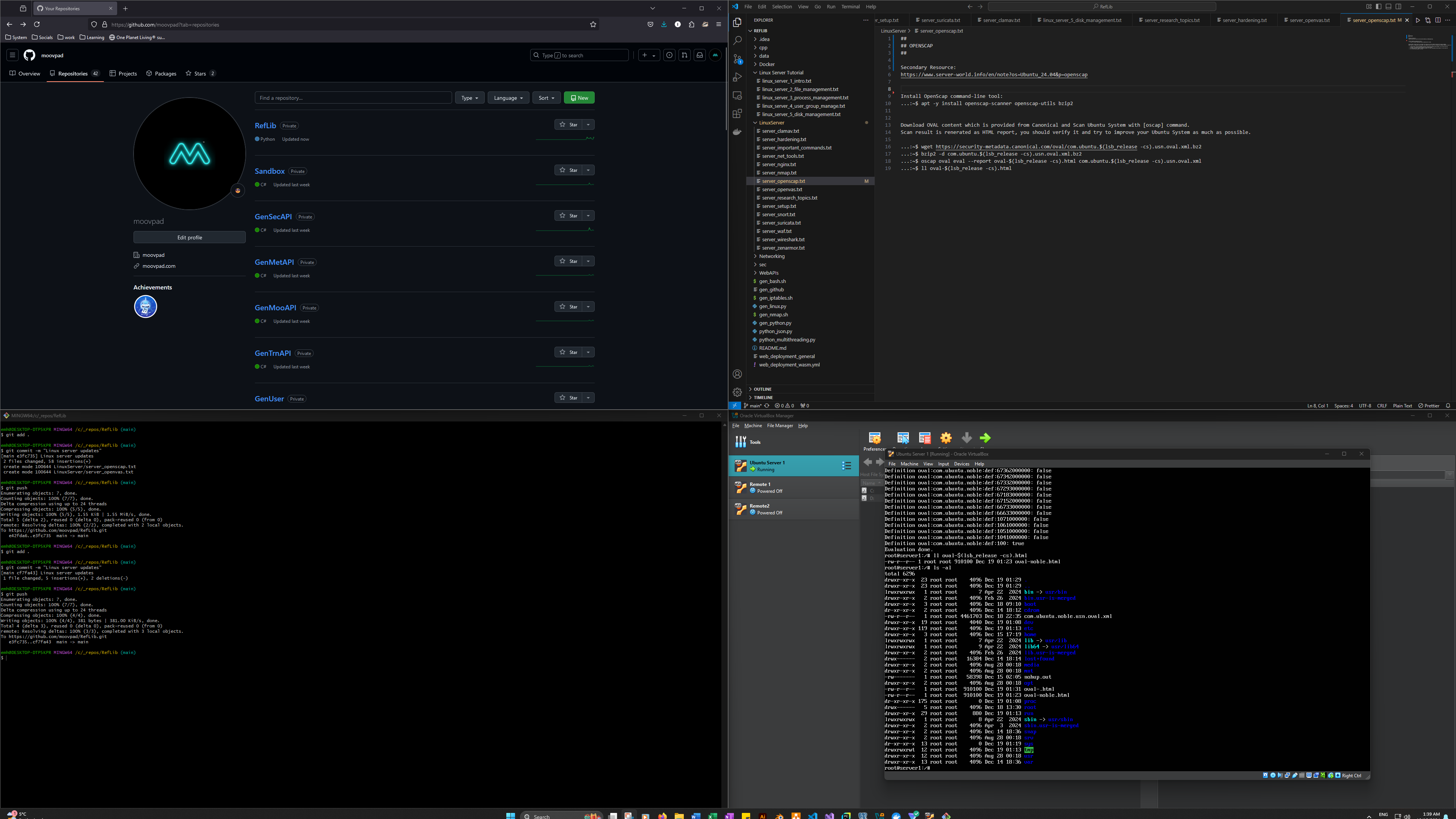
The second set of tools I want to implement is called OpenVAS. This scans for vulnerabilities as well, but goes further by allowing the scanning of things like web servers, containers and apps installed on the base system. To use these tools properly, I'll be setting up a linux-based test terminal which will eventually become a permanent feature of the server management workflow (for a few reasons).
Some good progress made, and I hope you guys have a great day ahead too 🙂
Stay awesome,
EMH
HOW MOOVPAD IS BEING BUILT
For the overview of how MOOVPAD apps are being developed, the reasoning behind particular decisions during development, policies, and more in relation to all the technical things, please see the link to the left.
This will be an ongoing work in progress, and will always be linked to the bottom of each upcoming Blog post.
